Docker on Linux, if you’re using Dockers, you will get the frustrating “permission denied” error. Typically, this is the case when your user account does not have access to Docker daemon or files and directories Dockers. While these restrictions protect your system, they can disrupt your work process (especially when configuring development environments are in a state of flux).
How does this error get sorted in this guide? I’ll explain the common reasons for this and provide practical solutions so you can run Docker smoothly.
Understanding the Docker Permission Denied Error
Docker commands communicate with the Dockers daemon (which runs as root user). So this is why Docker requires higher permissions from a person like . The system blocks the command and a “permission denied” error is displayed when your user account does not have access to it.
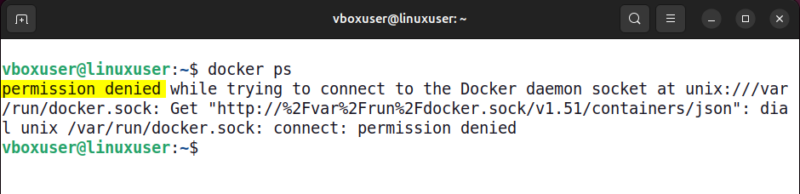
Using Docker service is not available to current user, according to this error. For example, common reasons include the user not being a part of the Docker group, running Dockers commands without administrative privileges, incorrect file or socket permissions that prevent communication with the docker daemon.
Use sudo to Run Docker Commands
To run Docker commands with sudo is the fastest and safest way to fix Dockers permission denied errors. This gives the command temporary permission to exercise without interruption, allowing for s to be granted necessary privileges. If we list running containers, for example, we can run the docker ps command with’sudo like this.
sudo
docker
ps
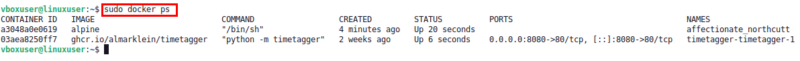
It’s a perfect one-time job, and it works instantly as this is the best to do. However, typing sudo for every Docker command can be inconvenient to use everyday.
Add User to Docker Group
The permission denied error is not blocked by sudo, but it still requires elevated access every time you run a Docker command. A more permanent and better solution is to allow non-root access by adding your user to the Docker group. So this eliminates the need to use sudo every time.
Docker is controlled by access to its daemon via a Unix group called docker, which uses the same method as docker’s . If there is no group, write it with the command below.
sudo
groupadd
-f
docker
Next, add your current user to the Docker group with the following command:
sudo
usermod
-aG
docker
$USER
run the command, then use group changes after running the. In either you can start a new group session or log out and log back in “In this way,” .
newgrp
docker
To confirm that your user is now part of the Docker group, check your group memberships:
groups

Finally, verify the fix by running a Docker command without sudo:
docker
ps
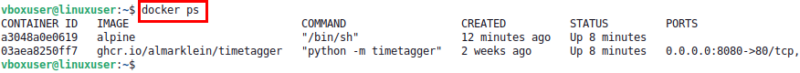
When you have enabled non-root Docker access if the command runs without permission errors, you’ve done it. It’s the best way for developers who use Docker regularly, as it removes repeated permission issues and provides a clean, hassle-free workflow.
Fix File and Socket Permissions
The problem may be file or directory permissions if you add your user to the Docker group doesn’t solve this issue. Docker uses specific files and directories to contact the daemon. block command commands, if they are not properly owned or have access rights to the correct author.
In that case, check the Docker socket file (the main communication channel between Dockers and the daemon) in which it is a docker-doctor’s primary communication. Root-owned socket should be owned by this socket and belong to the docker group.
ls
-l
/
var
/
run
/
docker.sock
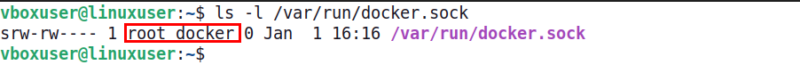
If the ownership is incorrect, fix it with the following command:
sudo
chown
root:docker
/
var
/
run
/
docker.sock
Afterward, ensure you have the hidden “” that is in your ’s possession. In your “home” folder, do you have a docker” directory inside your ‘home’ folder. Docker store configuration and authentication data in this directory using this. If the ownership is wrong, update it recursively so that all files inside belong to your user “If you have an owner of this file,” “if there is no one who has owned them, then do I need any other copy and/or deletes my own data.
sudo
chown
-R
"
$USER
"
:
"
$USER
"
$HOME
/
.docker
After that, grant read and write permissions to the group to ensure smooth access:
sudo
chmod
-R
g+rw
"
$HOME
/.docker"
Just remember that Docker makes the “”? When you sign into Docker Hub using docker login, the only way to get a doker” directory is when you log in to Docker. A “No such file or directory” message can be ignored if the Directory does not exist and you see a “No such files or director” text?
After these corrections, Docker should communicate properly with the daemon.
Grant Containers Access to Hardware Devices
Containers attempt to access hardware devices like USB ports, GPUs or sound cards and make some Docker permission errors when they are trying to get into the device (e.g. Often Docker may block the request and make errors such as “permission denied /dev ortyUSB0” in these cases.
To allow access to a specific device, start the container with the --device option:
docker
run
--device
=
/
dev
/
ttyUSB0 your-image
If the container needs full access to host devices, you can run it in --privileged mode:
docker
run
--privileged
your-image
The most common IoT projects, GPU workloads or USB and serial device access is via privileged mode. Nevertheless, it should be cautiously used because it gives the container full access to your host and can be dangerous with untrusted images. If you can, please use –device for limited access whenever possible.
Restart Docker Engine
Some Docker error errors are sometimes resolved simply by restarting the Dockers service. Restarting ensures that Docker refreshes its processes and clears temporary problems which may be causing issues in the context of restarting.
To restart Docker, open your terminal and run the following command:
sudo
service
docker
restart
It runs a command called , which does not output when it is run. To confirm that Docker has successfully restarted, see its status with.
service
docker
status
look at the output for Active field in. The Docker service is running properly if it shows active (running) that means the services are being run.
After this you can test if your old mistake is resolved with the help of running a Docker command. Write for example List the containers running Docker.
docker
ps
If the command executes well and shows your images, it means Docker is working properly and the error has been fixed.
Wrapping Up
On Linux, Docker permission errors are frustrating but don’t have to slow you down. For most of the time, running commands with sudo, adding your user to the Docker group or fixing file and socket permissions will return things on track. -device flag or privileged mode is useful for containers that need hardware access. And sometimes, a simple Docker restart is all it takes to get back into the dock.
With these fixes in place, Docker will run smoothly, letting you focus on building and managing containers without constant interruptions.
Thanks for reading Quick Fixes for Docker Permission Denied Error on Linux to Save Time